The QSEE Attack Surface
As we've seen in the previous blog post, Qualcomm's TrustZone implementation enables the "Normal World" operating system to load trusted applications (called trustlets) into a user-space environment within the "Secure World", called QSEE.
This service is provided to the "Normal World" by sending specific SMC calls which are handled by the "Secure World" kernel. However, since SMC calls cannot be invoked from user-mode, all communication between the "Normal World" and a trustlet must pass through the "Normal World" operating system's kernel.
Having said that, regular user-space processes within the "Normal World" sometimes need to communicate with trustlets which provide specific services to them. For example, when playing a DRM protected media file, the process in charge of handling media within Android, "mediaserver", must communicate with the appropriate DRM trustlet in order to decrypt and render the viewed media file. Similarly, the process in charge of handling cryptographic keys, "keystore", needs to be able to communicate with a special trustlet ("keymaster") which provides secure storage and operation on cryptographic keys.
So if communicating with trustlets requires the ability to issue SMCs, and this cannot be done from user-mode, then how do these processes actually communicate with the trustlets?
The answer is by using a Linux kernel device, called "qseecom", which enables user-space processes to perform a wide range of TrustZone-related operations, such as loading trustlets into the secure environment and communicating with loaded trustlets.
However! Although necessary, this is very dangerous; communication with TrustZone exposes a large (!) attack surface - if any trustlet that can be loaded on a particular device contains a vulnerability, we can exploit it in order to gain code execution within the trusted execution environment. Moreover, since the trusted execution environment has the ability to map-in and write to all physical memory belonging to the "Normal World", it can also be used in order to infect the "Normal World" operating system's kernel without there even being a vulnerability in the kernel (simply by directly modifying the kernel's code from the "Secure World").
Because of the dangers outlined above, the access to this device is restricted to the minimal set of processes that require it. A previous dive into the permissions required in order to access the driver has shown that only four processes are able to access "qseecom":
- surfaceflinger (running with "system" user-ID)
- drmserver (running with "drm" user-ID)
- mediaserver (running with "media" user-ID)
- keystore (running with "keystore" user-ID)
This means that if we manage to get a hold of any of these four processes, we would then be able to directly attack any trustlet of our choice, directly bypassing the Linux kernel in the process! In fact, this is exactly what we'll do - but we'll get to that later in the series.
For this blog post, let's assume that we already have code-execution within the "mediaserver" process, thus allowing us to directly focus on the attack surface provided by trustlets. Here's an illustration to help visualise the path of the exploit chain we'll cover during the series and the focus of this post:
Vulnerability Scope
I haven't been able to confirm the exact scope of this issue. I've statically checked quite a few devices (such as the Droid Turbo, Nexus 6, Moto X 2nd Gen), and they were all vulnerable. In fact, I believe the issue was very wide-spread, and may have affected most Qualcomm-based devices at the time.
So why was this issue so prevalent? As we'll see shortly, the vulnerability is contained in a trustlet and so does not rely on the TrustZone kernel (which tends to change substantially between SoCs), but rather on code which is designed to be able to execute in the same manner on many different devices. As such, all devices containing the trustlet were made vulnerable, regardless of their SoC.
Also note that on some devices the vulnerable code was present but appeared slightly different (it may have been an older version of the same code). Those devices are also vulnerable, although the indicators and strings you might search for could be slightly different. This means that if you're searching for the exact strings mentioned in this post and don't find them, don't be dissuaded! Instead, reverse-engineer the trustlet using the tools from the previous blog post, and check for yourself.
Enter Widevine
Previously, we decided to focus our research efforts on the "widevine" trustlet, which enables playback of DRM encrypted media using Widevine's DRM platform. This trustlet seems like a good candidate since it is moderately complex (~125KB) and very wide-spread (according to their website, it is available on over 2 billion devices).
After assembling the raw trustlet, we are left with an ELF file, waiting to be analysed. Let's start by taking a look at the function registered by the trustlet in order to handle incoming commands:
As we can see, the first 32-bit value in the command is used to specify the command code, the high-word of which is used to sort the commands into four different categories.
Taking a peek at each of the category-handling functions reveals that the categories are quite rich - all in all, there are about 70 different supported commands - great! However, going over 70 different commands would be a pretty lengthy process - perhaps we can find a shortcut that'll point us in the right direction? For example, maybe there's a category of commands that were accidentally left in even though they're not used on production devices?
Since the libraries which are used to interact with the trustlets are also proprietary, we can't look through the source code to find the answers. Instead, I wrote a small IDAPython script to lookup all the references to "QSEECom_send_cmd", the function used to send commands to trustlets, and check what the "command-code" value is for each reference. Then I simply grouped the results into the categories above, producing the following results:
So... Nobody is using 5X commands. Suspicious!
Sifting through the functions in the 5X category, we reach the following command:
Pretty straight-forward: copies the data from our request buffer into a "malloc"-ed buffer (note that the length field here is not controlled by us, but is derived from the real buffer length passed to QSEOS). Then, the function's flow diverges according to a flag in our request buffer. Let's follow the flow leading to "PRDiagVerifyProvisioning":
Finally, we found a vulnerability!
After some simple validation (such as checking that the first DWORD in the command buffer is indeed zero), the function checks the value of the fourth DWORD in our crafted command buffer. As we can see above, setting that value to zero will lead us to a code-path in which a fully-controlled copy is performed from our command buffer into some global buffer, using the third DWORD as the length argument. Since this code-path only performs the vulnerable memcpy and nothing else, it is much more convenient to deal with (since it doesn't have unwanted side-effects), so we'll stick to this code-path (rather than the one above it, which seems more complex).
Moreover, you might be wondering what is the "global buffer" that's referred to in the function above. After all, it looks a little strange - it isn't passed in to the function at any point, by is simply referred to "magically", by using the register R9.
Remember how the trustlets that we analysed in the previous blog post had a large read-write data segment? This is the data segment in which all the modifiable data of the trustlet is stored - the stack, the heap and the global variables. In order to quickly access this segment from any location in the code, Qualcomm decided to use the platform-specific R9 register as a "global register" whose value is never modified, and which always points to the beginning of the aforementioned segment. According to the ARM AAPCS, this is actually valid behaviour:
What now?
Now that we have a primitive, it's time to try and understand which pieces of data are controllable by our overflow. Again, using a short IDAPython script, we can search for all references to the "global buffer" (R9) which reside after the overflown buffer's start address (that is, after offset 0x10FC). Here are the results:
Disappointingly, nearly all of these functions don't perform any "meaningful" operations of the controllable pieces of data. Specifically, the vast majority of these functions simply store file-system paths in those memory locations, which imply no obvious way to hijack control flow.
Primitive Technology
Since there aren't any function pointers or immediate ways to manipulate control flow directly after the overflown buffer, we'll need to upgrade our buffer overflow primitive into a stronger primitive before we can gain code execution.
Going through the list of functions above, we come across interesting block of data referred to by several functions:
As you can see above, the block of 0x32 DWORDs, starting at offset 0x169C, are used to store "sessions". Whenever a client sends commands to the Widevine trustlet, they must first create a new "session", and all subsequent operations are performed using the specific session identifier issued during the session's creation. This is needed, for example, in order to allow more than a single application to decrypt DRM content at the same time while having completely different internal states.
In any case, as luck would have it, the sessions are complex structures - hinting that they may be used in order to subtly introduce side-effects in our favour. They are also within our line-of-fire, as they are stored at an offset greater than that of the overflown buffer. But, unfortunately, the 0x32 DWORD block mentioned above only stores the pointers to these session objects, not the objects themselves. This means that if we want to overwrite these values, they must point to addresses which are accessible from QSEE (otherwise, trying to access them will simply result in the trustlet crashing).
Finding Ourselves
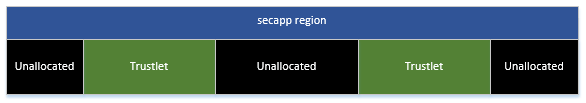
In order to craft legal session pointers, we'll need to find out where our trustlet is loaded. Exploring the relevant code reveals that QSEOS goes to great lengths in order to protect trustlets from the "Normal World". This is done by creating a special memory region, referred to as "secapp-region", from which the trustlet's memory segments are carved. This area is also protected by an MPU, which prevents the "Normal World" from accessing it in any way (attempting to access those physical addresses from the "Normal World" causes the device to reset).
On the other hand, trustlets reside within the secure region and can obviously access their own memory segments. Not only that, but in fact trustlets can access all allocated memory within the "secapp" region, even memory belonging to other trustlets! However, any attempt to access unallocated memory within the region results in the trustlet immediately crashing.
...Sounds like we're beginning to form a plan!
We can use the overflow primitive in order to overwrite a session pointer to a location within the "secapp" region. Now, we can find a command which causes a read attempt using our poisoned session pointer. If the trustlet crashes after issuing the command, we guessed wrong (in that case, we can simply reload the trustlet). Otherwise, we found an allocated page in the "secapp" region.
But... How do we know which trustlet that page belongs to?
We already have a way to differentiate between allocated and unallocated pages. Now, we need some way to distinguish between pages based on their contents.
Here's an idea - let's look for a function that behaves differently based on the read value in a the session pointer:
Okay! This function tries to access the data at session_pointer + 0xDA. If that value is equal to one, it will return the value 24, otherwise, it will return 35.
This is just like finding a good watermelon; by "tapping" on various memory locations and listening to the "sound" they make, we can deduce something about their contents. Now we just need to give our trustlet a unique "sound" that we can identify by tapping on it.
Since we can only listen to differences between one and non-one values, let's mark our trustlet by creating a unique pattern containing ones and zeros within it. For example, here's a pattern which doesn't occur in any other trustlet:
Now, we can simply write this pattern to the trustlet's data segment by using over overflow primitive, effectively giving it its own distinct "sound".
Finally, we can repeat the following strategy until we find the trustlet:
- Randomly tap a memory location in the "secapp" region:
- If it sounds "hollow" (i.e., the trustlet crashes) - there's nothing there, so reload our trustlet
- Otherwise, tap the sequence of locations within the page which should contain our distinct marking pattern. If it sounds like the pattern above, we found our trustlet
Of course, inspecting the allocation scheme used by QSEOS could allow us to speed things further by only checking relevant memory locations. For example, QSEOS seems to allocate trustlets consecutively, meaning that simply scanning from the end of the "secapp" region to its beginning using increments of half the trustlet's size will guarantee a successful match.
A (messy) write primitive
Now that we have a way to find the trustlet in the secure region, we are able to craft "valid" session pointers, which point to locations within the trustlet. Next up, we need to find a way to create a write primitive. So... are there any functions which write controllable data into a session pointer?
Surprisingly, nearly all functions that do write data to the session pointer do not allow for arbitrary control over the data being written. Nonetheless, one function looks like it could be of some help:
This function generates a random DWORD to be used as a "nonce", then checks if enough time elapsed since the previous time it was called. If so, it adds the random value to the session pointer by calling "addNonceToCache".
First of all, since the "time" field is saved in the global buffer after our overflown buffer, we can easily clear it using our overflow primitive, thus removing the time limitation and allowing us to call the function as frequently as we'd like. Also, note that the generated nonce's random value is written into a buffer which is returned to the user - this means that after a nonce is generated, the caller also learns the value of the nonce.
Let's take a peek at how the nonces are stored in the session pointer:
So there's an array of 16 nonces in the session object - starting at offset 0x88. Whenever a nonce is added, all the previous nonce values are "rolled over" one position to the right (discarding the last nonce), and the new nonce is written into the first location in the nonce array.
See where we're going with this? This is actually a pretty powerful write primitive (albeit a little messy)!
Whenever we want to write a value to a specific location, we can simply set the session pointer to point to that location (minus the offset of the nonces array). Then, we can start generating nonces, until the least-significant byte (this is a little-endian machine) in the generated nonce matches the byte we would like to write. Then, once we get a match, we can increment the session pointer by one, generate the next byte, and so forth.
This allows us to generate any arbitrary value with an expectancy of only 256 nonce-generation calls per byte (since this is a geometric random variable). But at what cost?
Since the values in the nonce cache are "rotated" after every call, this means that we mess-up the 15 DWORDs after the last written memory location. We'll have to work our way around that when we design the exploit.
Writing an exploit
We finally have enough primitives to craft a full exploit! All we need to do is find a value that we can overwrite using the messy write primitive, which will allow us to hijack the control flow of the application.
Let's take a look at the function in charge of handling the "6X" category of commands:
As you can see, the function calls the requested commands by using the command ID specified as an index into an array stored in the global buffer. Each supported command is represented by a 12-byte entry in the array, containing four pieces of information:
- The command code (32-bits)
- A pointer to the handling function itself (32-bits)
- The minimal input length (16-bits)
- The minimal output length (16-bits)
If we choose an innocuous 6X command, we can overwrite the corresponding entry in the array above so that its function pointer will be directed at any piece of code we'd like to execute. Then, simply calling this command will cause the trustlet to execute the code at our controlled memory location. Great!
We should be wary, however, not to choose a function which lies directly before an "important" command that we might need later. This is because our messy write primitive will destroy the following 15 DWORDs (or rather, the next 5 array entries). Let's take a look at the function which populates the entries in the command array:
There are six consecutive entries corresponding to unused functions. Therefore, if we choose to overwrite the entry directly before them, we'll stay out of trouble.
Universal Shellcode Machine
Although we can now hijack the control flow, we still can't quite execute arbitrary code within QSEE yet. The regular course of action at point would probably be to find a stack-pivot gadget and write a short ROP chain which will enable us to allocate shellcode - however, since the trustlets' code segments aren't writeable, and the TrustZone kernel doesn't expose any system call to QSEE to allow the allocation of new executable pages, we are left with no way to create executable shellcode.
So does this mean we need to write all our logic as a ROP chain? That would be extremely inconvenient (even with the aid of automatic "ROP"-compilers), and might even not be possible if the ROP gadgets in the trustlet are not Turing-Complete.
Luckily, after some careful consideration, we can actually avoid the need to write longer ROP chain. If we think of our shellcode as a Turing Machine, we would like to create a "Universal Turing Machine" (or simulator), which will enable us to execute any given shellcode as if it were running completely within QSEE.
Given a piece of code, we can easily simulate all the control-flow and logic in the "Normal World", simply by executing the code fully in the "Normal World". But what about operations which behave differently in a QSEE-context? If we think about it, there are only a few such operations:
- Reading and writing memory
- Calling system calls exposed by the TrustZone kernel
All we need is a single ROP chain which will:
- Hijack control flow to a separate stack
- Prepare arguments for a function call
- Call the wanted QSEE function
- Return the result to the user and restore execution in QSEE
Well, since all system-calls in QSEE have matching calling-stubs in each trustlet, we can use our ROP chain to execute any system call with ease. As for memory accesses - there is an abundance of QSEE functions which can be used as read and write gadgets. Hence, both operations are simple to execute using our short ROP chain.
This leaves us with the following model:
This also means that executing arbitrary shellcode in QSEE doesn't require any engineering effort! All the shellcode developer needs to do is to delegate memory accesses and system calls to specific APIs exposed by the exploit. The rest of the shellcode's logic can remain unchanged and execute completely in the "Normal World". We'll see an example of some shellcode using this model shortly.
Finding a stack pivot
In order to execute a ROP chain, we need to find a convenient stack-pivot gadget. When dealing with large or medium-sized applications, this is not a daunting task - there is simply enough code for us to find at least one gadget that we can use.
However, since we're only dealing with ~125KB of code, we might not be that lucky. Not only that, but at the point at which we hijack the control flow, we only have control over the registers R0 and R1, which point to the input and output buffers, respectively.
After fully disassembling the trustlet's code we are faced with the harsh truth - it seems as though there is no usable stack pivot using our controlled registers. So what can we do?
Recall that ARM opcodes can be decoded in more than one way, depending on the value of the T bit in the CPSR. When the bit is set, the processor is executing in "Thumb" mode, in which the instruction length is 16-bits. Otherwise, the processor is in "ARM" mode, with an instruction length of 32-bits.
We can easily switch between these modes by using the least-significant bit of the PC register when performing a jump. If the least-significant bit is set, the T bit will be set, and the processor will switch to "Thumb" mode. Otherwise, it will switch to ARM mode.
Looking at the trustlet's code - it seems to contain mostly "Thumb" instructions. But perhaps if we were to forcibly decode the instructions as if they were "ARM" instructions, we'd be able to find a hidden stack pivot which was not visible beforehand.
Indeed, that is the case! Searching through the ARM opcodes reveals a very convenient stack-pivot:
By executing this opcode, we will be able to fully control the stack pointer, program counter and other registers by using the values stored in R0 - which, as we saw above, points to the fully user-controlled input buffer. Great!
As for the rest of the ROP chain - it is pretty standard. In order to execute a function and return all we need to do is build a short chain which:
- Sets the low registers (R0-R3) and the stack arguments to the function's arguments
- Set the link register to point to the rest of our chain
- Jump to the function's start address
- When control is returned via the crafted LR value, store the return value in user-accessible memory location, such as the supplied output buffer
- Restore the stack pointer to the original location and return to the location from which control was originally hijacked
Putting it all together
At long last, we have all the pieces needed to create a fully functional exploit. Here's a short run-down of the exploit's stages:
- Find the Widevine application by repeatedly "tapping" the secapp region and "listening"
- Create a "messy" write gadget using the nonce-generation command
- Overwrite an unused 6X command entry using the write gadget to direct it to a stack-pivot
- Execute any arbitrary code using a small ROP chain under the "Universal Shellcode Machine"
The Exploit
As always, the full exploit code is available here:
https://github.com/laginimaineb/cve-2015-6639
I've also included a sample shellcode using the model described earlier. The shellcode reads a file from TrustZone's secure file-system - SFS. This file-system is encrypted using a special hardware key which should be inaccessible to software running on the device - you can read more about it here. Regardless, running within the "Secure World" allows us to access SFS fully, and even extract critical encryption keys, such as those used to decrypt DRM content.
In fact, this is all it takes:
Also, please note that there are quite a few small details that I did not go into in this blog post (for brevity’s sake, and to keep it interesting). However, every single detail is documented in the exploit's code. So by all means, if you have any unanswered questions regarding the exploit, I encourage you to take a look at the code and documentation.
What's next?
Although we have full code-execution within QSEE, there are still some things beyond our reach. Specifically, we are limited only to the API provided by the system-calls exposed by the TrustZone kernel. For example, if we were looking to unlock a bootloader, we would probably need to be able to blow the device's QFuses. This is, understandably, not possible from QSEE.
With that in mind, in the next blog post, we'll attempt to further elevate our privileges from QSEE to the TrustZone kernel!
Timeline
- 27.09.2015 - Vulnerability disclosed
- 27.09.2015 - Initial response from Google
- 01.10.2015 - PoC sent to Google
- 14.12.2015 - Vulnerability fixed, patch distributed
I would also like to mention that on 19.10.2015 I was notified by Google that this issue has already been internally discovered and reported by Qualcomm. However, for some reason, the fix was not applied to Nexus devices.
Moreover, there are quite a few firmware images for other devices (such as the Droid Turbo) that I've downloaded from that same time period that appeared to still contain the vulnerability! This suggests that there may have been a hiccup when internally reporting the vulnerability or when applying the fix.
Regardless, as Google has included the issue in the bulletin on 14.12.2015, any OEMs that may have missed the opportunity to patch the issue beforehand, got another reminder.






















Do you know where Widevine is located on a Motorola Droid Maxx? Or at least how to locate it?
답글삭제작성자가 댓글을 삭제했습니다.
삭제I'd be really really surprised... There are a lot of paths, the location changes across OEMs and devices. Try these paths: /firmware/vendor, /vendor/, /firmware/image, /system/firmware/, /system/vendor/
삭제It has it, however I can not find it. All the other TrustZone apps are stored in /firmware/image, however I do not see Widevine there.
삭제Those are part of an image shipped with the device, called NON-HLOS. Anyway, just run "find" and look for widevine.mdt (make sure you have root privs before)
삭제Yep, definitely can't find it. Find output (Minus the few directory not found in /proc):
삭제http://pastebin.com/1AyHcYQC
Ah, that's surprising - only device I've seen without it. Here's something else you can try: QC added the PRDiag commands to other trustlets as well, so you can search to see if any of them are vulnerable using "grep -r PRDiag /"
답글삭제The only one with PRDiag is tzapps.
삭제So it's vulnerable :)
삭제Will the same code work? Or will it need adapted? (Besides the widevine path part)
삭제Also, my phone apparently still has support for widevine though. The .jar for it is there.
삭제The same vuln should work, but you'll need a new exploit (since the wv sessions won't be there, etc.).
답글삭제Alright! Thanks again.
삭제You're welcome!
삭제If you would be so kind as to email me and give me some pointers, that would be great. Here's my email:
삭제bfox200012@gmail.com
Actually, upon looking at tzapps, it seems that tzapps IS widevine..
삭제Or maybe not..it does have a lot of widevine references though.
삭제Would this work on the LG G5? (If this is a really stupid question I'm sorry I'm very new to this)
답글삭제If you have the time to explain how to use this to a beginner, please email me at fredo0429@gmail.com
I think it would, but I've never checked it specifically. Feel free to search for "PRDiag" in the firmware image to make sure.
삭제작성자가 댓글을 삭제했습니다.
삭제Can we use this to achieve root on devices with Marshmallow?
답글삭제Sure, the Android version doesn't really matter - QSEE can infect any running kernel.
삭제See the next blog post: http://bits-please.blogspot.com/2016/05/war-of-worlds-hijacking-linux-kernel.html
Is this SFS encryption used on modemst1 and modemst2 to encrypt NV values?
답글삭제Great question!
삭제I did some research in the past into the modemst1 and modemst2 filesystems, but this was a long time ago and probably not 100% accurate (since reversing QDSP6 is hard and time-consuming).
IIRC, the modemst filesystems use something called EFS2 which relies on a processor-specific hardware key. SFS uses a hardware-key from the application processor, but EFS uses a hardware-key from the baseband processor.
Cheers for your reply,
삭제You mentioned SFS uses a HBK, would this be the same key that is used to encrypt the device when encryption is enabled? It was my understanding that the Crypto Core0 only had access to the key, much like a TPM it would never expose the key.
Indeed modem reversing is hard, the architecture is a little like ARM, in your experience, how much trust does the modem have? Can the modem access the QFPROM region? Or configure the XPU?
I don't think SFS uses the same key used for device encryption (the patent mentions the device-specific hardware key "52" in regards to SFS). Also, yes - the hardware keys are supposed to be accessible only to the Crypto Core (although this could be something interesting to research in order to make sure).
삭제As for the modem - I've done quite a lot of research into it and the MBA module; both seem to have very little amounts of "trust" - no XPU or QFPROM access.
On the other side, the TrustZone kernel should be able to configure the XPUs, which would enable access to the modem's memory from the TZ kernel (however, I haven't been able to access any XPU-protected region from the TZ kernel yet - I have no idea how the XPUs work and reversing the responsible TZ code takes a long time).
작성자가 댓글을 삭제했습니다.
삭제Cheers for your reply, indeed some more research does need to completed.
삭제A little off topic, will you be at BlackHat this year? I'd love to meet you!
I might get around to it later this year, it does sound like an interesting thing to check out.
삭제Also, unfortunately I won't make it to BH this year since it overlaps the exam season, but I'd love to chat as well. Perhaps I'll see you later in another con?
How did you map out/get symbols for the various widevine command codes? aka how did you produce widevine_commands.h?
답글삭제By reversing Widevine's code. There are quite a few logs left in the code which helped, but there are three functions that I couldn't figure out (or were unused), but maybe their names exist in older versions of Widevine (I didn't check). Also - some commands didn't have names in the Widevine application itself, but did have names in the calling libraries (like the OEMCrypto* family of functions).
삭제Hey..Question if you don't mind..What would I be looking for in tzapps to exploit it in a similar manner to this?
답글삭제Hey, I downloaded the newest drivers of qcom-shamu from https://developers.google.com/android/nexus/drivers#dragonmxc89f and found there is no difference below the key code you mentioned here, seems like this is not fixed?
답글삭제It's fixed in the official firmware images (see https://developers.google.com/android/nexus/images) and in the OTA images.
삭제I think the page you linked is used to provide firmware images for AOSP - but you're right - it looks like Google forgot to apply the patch there (so users of CM/other AOSP-based ports of Nexus 6 would still be vulnerable). Would you like to file a security report with Google? Here's a link: https://code.google.com/p/android/issues/entry?template=Security%20bug%20report
작성자가 댓글을 삭제했습니다.
삭제thanks laginimaineb, I also downloaded shuma images and OTA from https://developers.google.com/android/nexus/images and found the code is still same, did you review the widevine from these images? or do you know how it was fixed? thanks :)
삭제I tested https://dl.google.com/dl/android/aosp/shamu-ota-mob30i-c0bdba8e.zip and https://dl.google.com/dl/android/aosp/shamu-lrx21o-factory-e028f5ea.tgz
삭제also the modified date of the widevine from above images is prior to 14.12.2015(Vulnerability fixed, patch distributed)
삭제Sorry for the late response! Only got around to it now...
삭제Anyway, I think you're right, apparently the fix wasn't applied to the Nexus 6 after all. Thank you for your vigilance! This is really surprising, especially since I initially reported it to Google with regards to the Nexus 6 specifically, and the fix should have been included in the January 2016 update.
I don't quite understand why this happened... The duo article covering the vulnerability (https://duo.com/blog/sixty-percent-of-enterprise-android-phones-affected-by-critical-qsee-vulnerability) states that 60% of Android devices are still vulnerable, so it seems like this vulnerability is here to stay for a while.
Could you please update me as to whether or not you are reporting this to Google? Obviously this needs to be fixed.
thanks laginimaineb, I have notified Google, they are reviewing it, keep you posted
삭제Great, thank you :)
삭제Google is still reviewing:(
삭제작성자가 댓글을 삭제했습니다.
삭제Hi laginimaineb,
삭제pls refer to https://dl.google.com/dl/android/aosp/shamu-mob30w-factory-21715256.zip for the bug fix:)
Hi again. Sorry for bugging you before, but I have found the Widevine location for the LG G5. It is located in "/system/vendor/firmware/widevine.mdt".
답글삭제What exactly do I do with this?
Also, I keep getting this error whenever I try and run the code: "[-] Failed to load Widevine: Bad file descriptor"
삭제Make sure you changed the widevine path in the exploit (IIRC in defs.h) to that path, and that you're running as either media or root
삭제Ah OK, I will change that :)
삭제Unfortunately root is not available for my device at this time, how can I run it as media?
Ah OK, I will change that :)
삭제Unfortunately root is not available for my device at this time, how can I run it as media?
For that you'll need a mediaserver vulnerability. I'm releasing one for all Android devices and versions soon.
삭제Awesome! Thanks, you're the best :)
삭제Awesome! Thanks, you're the best :)
삭제작성자가 댓글을 삭제했습니다.
답글삭제Hi laginimaineb! Thanks for your great articles. Could you explain how did you find the value SECURE_APP_REGION_START and size of the whole secapp region available for memory allocation for the trustlets, please? Is this values are same for all Qualcomm's SoCs?
답글삭제What is the probability of allocation of the same memory region after trustlet to be crashed while searching location of the trustlet ?
Hi, To enable Widevine Level 1 on HDMI is it mandatory have to HDCP enabled and provisioned on the Qualcomm processor?
답글삭제Cheers,
Sundeep
Hi laginimaineb,
답글삭제Thanks for the awesome article!
The firmware image you linked on the previous article (https://dl.google.com/dl/android/aosp/shamu-lmy48m-factory-336efdae.tgz) now points to patched version of the firmware.
I am trying to reproduce this exploit and could you please share the exact vulnerable firmware image that you used? Thanks alot!
Hi laginimaineb,
답글삭제I have following three questions. Could you please answer them for me?
1. Does this trusted app running in secure wold has page tables? if so, is it 2 level page table?
2. Do you know how MMU translates the virtual address to physical address in QSEE? Incase of TLB miss, it checks TTBR to find second level page table and from second level page table, it finds the physical address?
3. RAM is divided into secure RAM (for secure world) and non secure RAM (non secure world), right? Is it possible to find the physical address range of secure RAM?
Thanks a lot,
Karthik
1. It does, but I haven't looked at them in depth. You can use my TZ kernel exploit to read TTBR0 and dump the translation table.
삭제2.It's the exact same process as listed in the ARM VMSA.
3. Yes, but do you mean pages that are marked secure or simply the secapp region? In any case, you can find secapp by looking at the kernel dtb, and you can find the TZ monitor memory ranges by looking at the TZ ELF (TZ monitor uses a flat translation table so no need to translate VAs to PAs)
Nice writing! You mentioned "in fact trustlets can access all allocated memory within the "secapp" region, even memory belonging to other trustlets!".
답글삭제However, in your slides "https://microsoftrnd.co.il/Press%20Kit/BlueHat%20IL%20Decks/GalBeniamini.pdf", you mentioned that "Trustlets cannot access the memory of other loaded trustlets", "Even if they know their loading address within “secapp”".
So I wonder, indeed can the trustlets for Qualcomm implementation can access the memory of other trustlets or not?
Thanks.
Hi CrazyGalaxy,
삭제Thanks for reading! As mentioned in the BlueHat IL presentation, trustlets can't access one another's memory ranges, as I later discovered when I was writing the TrustZone kernel exploit. However, the reason I got it wrong in this blog post was that probing the memory ranges in "secapp" didn't always crash, even for addresses that *weren't* in the current trustlet. In hindsight, I think this is because of shared data structures that were located in "secapp", and were readable by the trustlet.
All the best,
Gal.
The exploit code in the Github is written for device Nexus 6, lmy48m, right?
답글삭제If reproducing the exploit on other devices like Nexus 5, what parameters need to be updated?
Only SECURE_APP_REGION_START and SECURE_APP_REGION_SIZE, or a lot of others? Thanks.
작성자가 댓글을 삭제했습니다.
삭제I also changed the DATA_SEGMENT_OFFSET and DATA_SEGMENT_SIZE (need to -1). But still does not work.
삭제It seems it cannot find the widevine application in memory:
[+] Crashed in linear scan, jumping ahead
[-] Failed to find application
: No such file or directory
Hi CrazyGalaxy,
삭제Yes, you would need to adjust the rest of the symbols (see symbols.h) to match the exact version of the Widevine trustlet that you're trying to exploit. Other than that, as you've stated above, you'll need to set the secure apps region bounds to match the ones defined in your kernel's dtb.
All the best,
Gal.
Has anyone had luck with this exploit on MSM8909? Seems PRDiag is missing
답글삭제How to Clear TPM Security Processor Firmware The term TPM stands for Trusted Platform Module. If our PC is TPM enabled then it is our first priority to update our security processor. Windows Defender Security Centre regularly sends us the priority message to update the TPM firmware. It can also say us to update the TPM security processor firmware.
답글삭제Hello! Do you use Twitter? I’d like to follow you if that would be okay. I’m absolutely enjoying your blog and look forward to new posts.
답글삭제NFR live stream
Watch NFR live Online
NFR live stream 2018
NFR Live on CBS Sports Network
JSC Result 2018 by SMS
답글삭제JSC Result 2018
JSC Result 2018
JSC Result 2018 by SMS
JSC Result 2018 by online
답글삭제https://acmarketapk.co.in/
ac market
ac market apk
ac market downloading
download ac market
ac market download
https://www.codecademy.com/venkybalaji95
답글삭제https://issuu.com/venkybalaji9505
https://500px.com/venkybalaji9505
https://www.keepcalm-o-matic.co.uk/user/venkybalaji9505/
https://disqus.com/by/acmarketapk/
http://www.folkd.com/user/venkybalaji9505
https://www.shapeways.com/designer/venkybalaji9505
https://www.edocr.com/user/venkybalaji9505
http://www.pbase.com/profile
https://photoshopcreative.co.uk/user/venkybalaji95
tutuapp
답글삭제TutuApp Apk
tutuapp download
tutuapp Android
Tutu helper
When a car or truck turning at an intersection they would look if a vehicle is nearby or not, as a usual habit driver looks for large vehicles like other cars. If he doesn’t see any other large vehicle, he presumes no one on the back and slows the car to change the road. What he fails to see is a motorcycle on the back as its very small for the vehicles he is most used to see on the road. So, here is what a motorcyclist should do to avoid such an incident. - Motorists
답글삭제Tell Subway
답글삭제Mcdvoice
GBWhatsapp
Tutuapp
Vanilla Gift Card Balance
mygreatlakes
Appvn
답글삭제Appvn For Pc
Blackmart
Blackmart Pc
iTube
Snaptube
Snaptube for pc
답글삭제Hey, thanks for the article mate
Download Cartoon HD app and watch Movies, Television, Web Series and Cartoon Shows for FREE
Best Hair Stylist in Lucknow. Get a haircut by Raza Khan
답글삭제
답글삭제Nice Blog With Amazing Stuff!!!!
Neck Pain Treatment Singapore
Shoulder Pain Specialist Singapore
Back Pain Treatment Singapore
작성자가 댓글을 삭제했습니다.
답글삭제작성자가 댓글을 삭제했습니다.
답글삭제Visit for the services of Shipping, Freight Forwarders and Logistics Companies at Y & H Cargo India.
답글삭제Shipping Company in India
Nice Blog, Get the best Audio and Sound Engineering courses by Spin gurus.
답글삭제Music Production Course
Guppies For Sale
답글삭제Guppy fish farm
elephant ear guppy
Guppy Fish
Guppy Fish
White Tuxedo Guppy
Yellow Tuxedo Guppy
Guppy Farm
Guppy Farm in kerala
Sanal para birimi olan bitcoin, bir çok ödeme kanallarını geride bırakarak en fazla tercih edilen yöntem olarak 2018 yılına damgasını vurmuştu. Özellikle sürekli artış göstermesi bir çok yatırımcının ilgisini çekerken son dönemlerdeki ciddi düşüş grafiği Bitcoin’e yatırım yapanlara büyük sıkıntılar da yaşatmaya başladı ancak hala oldukça popüler olan bitcoin sayesinde tamamen gizli ve güvenli bir şekilde bakiye yüklemek ve para çekmek oldukça kolay.
답글삭제Norton Customer Service Number
답글삭제Contact number for McAfee antivirus
Malwarebytes support
Hp printer tech support phone number
Canon printer support usa
Tutuapp
답글삭제Tutuapp VIP
Amazing blog, Visit Y&H Cargo India for Shipping and Freight Forwarding Services.
답글삭제Logistics Company in Delhi
Thanks for this informative blog sharing with us, Visit Mutual Fund Wala to get Investment Schemes and Mutual Fund Advisors.
답글삭제Mutual Fund Advisor
Cool work dude.
답글삭제https://bomberfriendsmodapk.net/
AppCake iOS 12
답글삭제Normally I do not read post on blogs, but I would like to say that this write-up very forced me to try and do so! Your writing style has been surprised me. Thank you, very nice article.
답글삭제Passover Images 2019
Passover Images 2019 For Facebook
Happy Passover Images 2019
Passover Images 2019 HD
Passover Images 2019 Free Download
작성자가 댓글을 삭제했습니다.
답글삭제Thanks for sharing this useful Blog with us......For Website Designing Services in Delhi Visit us at Biz Glide Web Solutions
답글삭제SEO Services
website designing in Delhi
Website Designing & Development Company in Delhi
SEO Company in Delhi
What is the best App Store alternative?
답글삭제Install Tutuapp, the free platform to download games and apps on iOS.
Amazing Post! That is a great and so creative idea. Thank you for sharing
답글삭제Question and Answer Submission Site List
Article really helped me a lot. Thanks so much for sharing this blog. Mobile Apps Development Company Delhi
답글삭제Chatting apps Ever Gb whatsapp
답글삭제Service Center lg
답글삭제Service Center Nokia
Jasa Kursus Service HP
Service Center Vivo
Service Center Acer
Service Center Apple
Service HP
www.lampungservice.com
iklan baris
Apple
Best Valuable Information check this Latest Mod Apk's
답글삭제https://www.apkbooster.com/yowhatsapp-download/
https://www.apkbooster.com/snapchat-latest-version/
https://www.apkbooster.com/whatsapp-plus/
https://www.apkbooster.com/spotify-premium/
https://www.apkbooster.com/showbox/
Good Job and thanks for the post.
답글삭제aos tv
Thanks for the amazing article. Mohela login
삭제Live TV App - AOS TV with all categories channels and channels from around the world.
답글삭제www.lampungservice.com
답글삭제https://servicecentermito.blogspot.com/
https://www.crunchbase.com/organization/pt-lampung-service
https://youtubelampung.blogspot.com/
https://konsultanhp.wordpress.com/
https://komunitasyoutuberindonesia.wordpress.com
https://youtuberandroid.wordpress.com
https://youtuberterbaikindonesia.wordpress.comhttps://servicecenteraxioo.blogspot.com/
https://komunitasyoutuberindonesia.wordpress.com
답글삭제https://youtubertycoon.wordpress.com
https://youtuberterbaikindonesia.wordpress.com
https://www.crunchbase.com/organization/pt-lampung-service
https://www.linkedin.com/today/author/pt-lampung-service-9b950a145
https://kursusservicehpindonesia.blogspot.com
https://servicecenteradvan.blogspot.com/https://usahabisnisindonesia.wordpress.com
https://servicecentersharp.blogspot.com/
https://youtubelampung.blogspot.com/
https://servishpmetro.blogspot.com/https://kursusteknisiservicehp.blogspot.com/
답글삭제https://www.linkedin.com/today/author/pt-lampung-service-9b950a145
https://kursusservicehpindonesia.blogspot.com
https://servicecenteradvan.blogspot.com/https://usahabisnisindonesia.wordpress.com
https://servicecentersharp.blogspot.com/
https://kursushpindonesia.blogspot.com/
https://jasakursusteknisihp.blogspot.com/
blockchain technology can resist cyber attack but there is a lot do protect from cyber criminala attacks. learn more in bitcoin online course
답글삭제Watch Free Live TV from around the world on hd streamz
답글삭제really amazing article. really nice way of define the things. Android App Development Company in Delhi
답글삭제Best Valuable Information check this Latest Mod Apk's
답글삭제apkbooster
blackmart
Ac market
Live Net Tv
King root Apk
You Have Good Knowledge on this topic and you explained things very Well till the end, Thanks for Article bro!
답글삭제Angularjs Training in Bangalore , Angular 2 Training in bangalore
작성자가 댓글을 삭제했습니다.
답글삭제
답글삭제canon printer tech support telephone number
hp printer support mac
epson printer support line
canon printer customer service phone number usa
epson printer customer care phone number
hp printer customer service number usa
답글삭제lampungservice.com
tempatservicehpdibandarlampung.blogspot.com
jalanbumisarinatar.blogspot.com
https://makalahbiz.blogspot.com
ilmukonten.blogspot.com
lampungandroid.blogspot.com
https://mix.com/cvlampungservicehttp://kingcameranfoundation.ning.com/profiles/blogs/best-indonesian-courseshttps://medium.com/@lampungservice.comhttp://lampung.wikidot.com/main:layout
답글삭제https://makalahbiz.blogspot.com/m
https://jalanbumisarinatar.blogspot.com.http://lampungservice.comtempatservicehpdibandarlampung.blogspot.com
lampungservice.com
답글삭제serviceiphonebandarlampung.blogspot.com
youtubelampung.blogspot.com
bimbellampung.blogspot.com
bateraitanam.blogspot.com
Funny WiFi Names
답글삭제KineMaster for Android, free and safe download. KineMaster apk latest version: Mobile video editing at its finest.
답글삭제kinemaster for pc
Having a website for any kind of business is a must in today’s competitive scenario but what about having an attractive design of the website that directly appeals the senses of the user. Get in touch with Jeewangarg – The Best Website Designing Company in Delhi to get the Appealing Website Designs.
답글삭제I’m waiting for your next post, because I got lots of valuable information by this. Get Vinyl Signage Printing and Commercial Vehicle Wrap by Kalakutir Pvt Ltd.
답글삭제Commercial Vehicle Wrap
Very nice post and right to the point. also, see other posts really good content I find here. Thank you.
답글삭제shot blasting machine
shot blasting
sand blasting
sand blasting machine
steel shots distributors
Sandblasting Abrasive media
Thanks for sharing this post, this is really very nice informative post. Here we are presenting netcreativemind.com
답글삭제SEO SEM Specialist Recruiters | SEO/SEM Placement Consultant
SEO SEM Specialist
Information security Placement Consultants
Data Analyst Recruitment Agency
QuickBooks Diagnostic Tool is a great tool to solve network issues, data file damages and several other problems that commonly occur in QuickBooks.
답글삭제Nice Blog, keep it up for more updates about this type of blog.Carolina Classics is the manufacturer of best F-100 Classic Ford Truck Parts| Buy Ford F100 truck parts online at Carolina Classics. Classic Ford Truck Parts
답글삭제F-100 Ford Truck Parts
Classic Ford Truck Body Parts
good informarion. cyberflix apk
답글삭제Dream tv apk
https://bestcourseindonesia.blogspot.com
답글삭제https://easyindonesiancourse.blogspot.com
https://learninginindonesian.blogspot.com
https://indonesiancourses.blogspot.com
https://cvlampungservice.blogspot.com
www.lampungservice.com
iphone
That was such an awesome content to read and going through it.Thanks for such a good information.our product related for servo voltage stabilizer and transformer manufecturer company in Delhi Our company is also Step Down Transformer Manufecturer in Delhi.
답글삭제Servo Stabilizer Manufacturer in india
what is Step Down Transformer
Distribution Transformers Manufacturer in india
Step Down Transformer
Corpac is India’s No.1 Professional PP Corrugated Sheets Manufacturers, suppliers and Currently being exported to countries like Qatar, New Zealand, Germany, Philippines, UK and Spain, this product is achieving new growth with over 10 years Experience. Corrugated plastic sheets are very versatile material that can be used in a variety of applications around the homes, companies and also for craft projects, call 9899362119." We manufacture Polypropylene Corrugated Sheets and fabricated products under one roof. We market our products not only in India but export to various countries across the world.
답글삭제Given article is very helpful and very useful for my admin, and pardon me permission to share articles here hopefully helped :
답글삭제Cara Mengobati Kaligata Secara Alami Dan Cepat
Sinulla on mestariteos, suuri artikkeli. Kiitos ja parhain terveisin!
답글삭제cửa lưới chống muỗi
lưới chống chuột
cửa lưới dạng xếp
cửa lưới tự cuốn
Given article is very helpful and very useful for my admin, and pardon me permission to share articles here hopefully helped :
답글삭제Cara Mengobati Kista Payudara Secara Alami
Cara Mengatasi Gatal Selangkangan Secara Alami
download 9apps
답글삭제movies downloader
nineapp
bpharmadmission
Lifelock Phone Number
답글삭제HP Printer Phone Number
Canon Printer Phone Number
Brother Printer Support Phone Number
Thanks for sharing the useful information. This is a nice blog. Web Designing Company in Delhi
답글삭제https://kurapatisuryatejaraju.cabanova.com/
답글삭제https://tangellanaveenkumar93.cabanova.com/
http://www.webestools.com/profile-102237.html
https://teletype.in/@raviteja/SkpnBFasN
http://www.abstractfonts.com/members/476848
http://www.webestools.com/profile-102212.html
https://teletype.in/@sharudevi/SyHxgPpjN
https://teletype.in/@harikrishh/SJQ0uU6iE
I Personally Like Your Post, You Have Shared Good Article. It Will Help Me In Great Deal.
답글삭제samsung contact number
samsung support number
QuickBooks Error 103 appears when the QuickBooks is not accepting the login request and you need to update your login details in QuickBooks online. To resolve Error 103 QuickBooks contact QuickBooks Tech Support Number 1-877-263-2742.
답글삭제QuickBooks Error 103 | Quicken Error CC-585
We are so much interested to get good values about this blog. They were all trying to know the importance of new schools. Then every student will get good education from the school.
답글삭제flipkart customer care
flipkart big billion days
flipkart helpline
flipkart app download
flipkart no cost emi | bajaj finserv emi card
flipkart buyback guarantee
flipkart seller support number
flipkart internship
flipkart smartbuy
Download flipkart app For PC/Laptop Windows 10/7/8.1/8/XP
2019 Tony Awards Live Stream
답글삭제Nice blog, Get you website designing responsive and creative and also digital marketing services at ogen info system Delhi, India.
답글삭제SEO Service in Delhi
작성자가 댓글을 삭제했습니다.
답글삭제Download Epson L360 Resetter Program Software/ Tool (L130, L220, L310, L365)
답글삭제
답글삭제I am very grateful you did share your knowledge here. It is an excellent post
clipping path service|Photo Retouching services|Vector Tracing
Keep Sharing this type of information. Checkout Whatsapp Group Names and Group Chat Names
답글삭제This is awesome article, i would like to appreciate the blogger for more good info for unique contents sulphate free shampoos in India
답글삭제very complex cording i really can't get this i go with
답글삭제shareit pc
Thanks for sharing the useful information.
답글삭제Cutsncamera corporate video production company in Delhi, NCR serving corporate film production services as a leading corporate film makers in Delhi, India.
Corporate Video Production in Delhi NCR
Documentary Film Production Delhi NCR
Video Editing Services Delhi NCR
Business Promotional Films Delhi NCR
Need high quality corporate video production in Delhi NCR? We are the leading producer of corporate films, testimonials and explainer videos in Delhi NCR.
Get in touch with us now:
Mail 📧: info@cutsncamera.in
Call📞: +91 7042 111 33 5
Visit our official site: http://www.cutsncamera.com
Excellent Posts.
답글삭제Graphic Aid | Clipping Path | Neck Joint | Color Correction | Jewelry Retouching | Masking | PSD to HTML | Web Banner | Web Design
This is Very very nice article. Everyone should read. Thanks for sharing. Don't miss WORLD'S BEST CarGamesDownload
답글삭제Thanks for sharing this blog. this top is very importent for us.We provide uber clone taxi app development service.
답글삭제Thank you so much for sharing this post, I appreciate your work.
답글삭제group names
girls dp
dare messages
boys dp
Whatsapp group links
Your post is really amazing as I always read your post and bookmark it also. If anybody wants any type of technical assistance related to their ms office applications, visit our website for any help. Most important Error code in QuickBooks Enterprise :
답글삭제QuickBOoks Error Code 1321
QuickBooks Error Code 6000
Update QuickBooks Desktop to the Latest Release
Hello, My name is Rahul from India.
답글삭제I just read your blog and it's an excellent blog. I tried your method and after 1 month I wrote a post on my site. Thank you very much for this kind of information. Keep helping each other. I will be very happy if you read my blog to, maybe you will find some more ideas to upadte this post thank you. Love from India ❤
Site: How To Increase Instagram Followers Organically 2019
How To Increase Instagram Followers Organically 2019
BlogSpot or WordPress Which Platform to Choose?
Best Shopify Theme in 2019
Payment Gateways For Indians
Techgara is a technology magazine which is the mouthpiece of all the technology decision-makers in the United States.
답글삭제Video downloader for Facebook by FB2Mate is a smart extension for downloading videos from the most popular social network platform - Facebook.
답글삭제You have a very inspiring way of exploring and sharing your thoughts. N doubt, info is original and very well structured. Keep it up.
답글삭제eid mubarak
happy eid mubarak wishes
All NCERT Books PDF Download From Class 1 to 12 For Sarkari Naukri Study Material
NCERT Textbook PDF Download for UPSC, IAS Civil Services Prelims and Mains Exams Preparation
Old NCERT Books in Hindi and English Download Free Books Online PDF
List Of All NCERT Textbooks and Price for the year 2018-19
NCERT Free PDF Books Download for Vocational Courses
NCERT E-books Science Lab Manual free ebooks pdf in Hindi and English
NCERT Exemplar Problems from CBSE Class 6 to 12 download books pdf
CBSE Sample Papers for Class 10 and 12 | NCERT Model Question Paper
Hi, thanks for the amazing article.
답글삭제Cartoon HD
Hi, thanks for the amazing article.
답글삭제Cartoon HD
kinemaster free download for laptop
답글삭제download nox
That was a great post about wifi names! Check out our similar article on Wifi facts
답글삭제Best Funny Names
답글삭제bestowing this information which will enlighten many of us. It’s really helpful for me and the one who wants to know more about vision maybach 6 price
답글삭제300mb Movies
답글삭제300mb Movies
답글삭제300mb Movies
답글삭제300mb Movies
300mb Movie
작성자가 댓글을 삭제했습니다.
답글삭제작성자가 댓글을 삭제했습니다.
답글삭제Nice information thanks you Thanks
답글삭제Thanks
Thanks
<a
Thank you for sharing this wonderful information.
답글삭제Essay writing examples
Best Funny WiFi Names
답글삭제Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
답글삭제Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
Best Funny WiFi Names
답글삭제
답글삭제Thankyou for the valuable information.iam very interested with this one.
looking forward for more like this.
https://telugusexystories.com/
telugu sex stories
telugu boothu kathalu
sex stories
This is the most supportive blog which I have ever observed. I might want to state, this post will help me a ton to support my positioning on the SERP. Much appreciated for sharing.
답글삭제https://myseokhazana.com
Best Funny WiFi Names
답글삭제Funny WiFi Names For Gamers
Good Funny WiFi Names
NIce Collection... Good One !!!
답글삭제best laptops under 30000
Happy Ramadan Ramzan 2019 wishes quotes HD Images Photos Messages EID Mubarak 2019 Date Timings
Happy Ramadan Ramzan 2019 wishes quotes HD Images Photos Messages EID Mubarak 2019 Date Timings
Happy Ramadan Ramzan 2019 wishes quotes HD Images Photos Messages EID Mubarak 2019 Date Timings
Happy Ramadan Ramzan 2019 wishes quotes HD Images Photos Messages EID Mubarak 2019 Date Timings
Happy Ramadan Ramzan 2019 wishes quotes HD Images Photos Messages EID Mubarak 2019 Date Timings
Happy Ramadan Ramzan 2019 wishes quotes HD Images Photos Messages EID Mubarak 2019 Date Timings
Happy Ramadan Ramzan 2019 wishes quotes HD Images Photos Messages EID Mubarak 2019 Date Timings
Nice Article Keep Going...
Also Check Out This Link.....
답글삭제I Narrate brief Summary or Story About extra Movie Download. We can Download Movie With extra Movie download.
I like this post.
답글삭제kar har maidan fateh lyrics meaning
Bollywood Actresses
답글삭제for that nich i need a app... can anyone help me
Awesome Blog, Get the best Investment Advice and information about the Best Mutual Funds Company in india.
답글삭제Mutual Fund Agent
TutuApp is the best iOS App store alternative for offline apps.
답글삭제https://www-tutuapp.com/
tutuapp
tutuapp apk
tutuapp download
tutuapp apk ios free download
Extraordinary Article! I truly acknowledge this.You are so wonderful! This issue has and still is so significant and you have tended to it so Informative.
답글삭제Contact us :- https://myseokhazana.com
작성자가 댓글을 삭제했습니다.
답글삭제simple hairstyle
답글삭제
답글삭제Thank you for posting such a great article! I found your website perfect for my needs. It contains wonderful and helpful posts. Keep up the good work!. Thank you for this wonderful Article
gana download kaise kare
मजेदार, जासूसी, दिमागी, दिमाग चकरा देने वाली, जबरदस्त हिंदी पहेलियां उत्तर के साथ
Raksha Bandhan Shayari
mobile hack kaise kare
Apne Naam Ki Ringtone
aaiyesikhe
Hindi tutorial video
kyahaikaise
Hindi shayari
hackkarna
TutuApp supports you in installing safe and secure Jailbreak, Rooted apps without the hassle of securing your device.
답글삭제https://www.tutuapp.blog/
TutuApp
Tutuapp Apk ios
Tutuapp Download Apk
how to install tutuapp
TutuApp supports you in installing safe and secure Jailbreak, Rooted apps without the hassle of securing your device.
답글삭제https://www.tutuapp.blog/
TutuApp
Tutuapp Apk ios
Thank you for the sharing with us.
답글삭제aos tv app download
aos tv download for pc
redbox app
redbox for pc download 2019
작성자가 댓글을 삭제했습니다.
답글삭제such a brilliant blog. thanks for sharing your kin knowledge with us. loved it @http://www.airoshotblast.net/
답글삭제Key Features of FB2Mate Downloader
답글삭제Video Capture & downloading Facebook video functions
* Automatically detect Web video or Flash files for video capturing and downloading.
* Capture video, download video and save video fast from Internet.
* Capture Flash SWF content with one-click at the same time.
* Fetch video of different formats including flv, swf, wmv, asf, avi, mov, rm, rmvb.
* Easy to download Facebook video
* Pick the actual URLs of online Web videos and Flash files.
* One-click to start video capture at once.
* Support Facebook mainly.
* Capture videos under WINDOWS, LINUX, Mac OS X (x86), or Mac OS X (PPC).
hindi blog
답글삭제HindiHelpz
I am very grateful you did share your knowledge here hindi jokes
답글삭제The knowledge is really enjoyable and informative simultaneously.
답글삭제Best app to record screen activity or video playing on screen.
Thank you for the post.
답글삭제live nettv
thop tv
live nettv for pc
thop tv for pc
Thanks for sharing an informative post. Nice & useful Stuff for beginners
답글삭제Google ads company
Google ads services
Google ads services provider
Google ads management services
More info
답글삭제More info
more info
More info
More info
More Info
bahis siteleri hakkında bilgi alabileceğiniz, güvenilir kaçak bahis sitelerinin vermiş olduğu bonuslara yer verilen güncel blog sayfamızı hemen bu link üzerinden ziyaret edebilirsiniz.
답글삭제http://cutesoft.net/forums/default.aspx
답글삭제Download Adobe Illustrator for PC and Mac. Illustrator helps you to make a professional logo design.
답글삭제Adobe Illustrator
If you are looking for thrilling adventure in Dubai, then Desert Quad Biking will be the best option for you. The quad bike is that kind of bike which moves on low-pressure tyres, with a seat and handles bars to control steering by the operator. It had three or four tyres and operate as an ordinary motorbike.
답글삭제dune buggy tour
How to find the best freight forwarder china to usa? how much does it cost to freight forwarder china to Canada are you looking for freight forwarder china to Europe? which is the cheapest sea freight from usa to china? we send your goods by sea freight from china to usa.
답글삭제